HIPAA Compliance for Access Control #
HIPAA refers to the Health Insurance Portability and Accountability Act of 1996 which was introduced by the US administration of that time in order to ensure the safety and security of the electronic Protected Health Information (PHI). PHI is the information of the common people and patients that have been associated to a health clearing agent or a health insurer. The HIPAA concentrates on the safekeeping and protection of these records. The figure below provides a basic idea of what features are required to analyze when examining the HIPAA compliance, this article will focus on HIPAA physical safeguards.
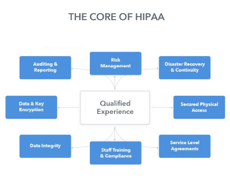
HIPAA’s effectiveness is based on its access control compliance of the administrative, technological, and physical access. When considering the HIPAA physical safeguards, the importance of e-PHI must not be diminished as these Protected Health Information documents are in the form of scanned images, pdf files and other database records.
The basic parameters for HIPAA access control compliance in terms of physical security domain are considered to be: Facility Access Controls, Workstation Use, Workstation Security and Devices and Media Controls.
- Physical safeguard or Facility Access Controls: The physical security of server rooms and other related physical structure which supports and holds the PHI documents.
- Workstation Use: the safe utilization of associated workstations like computers to the main server.
- Workstation Security: a secure system or procedure that ensures the physical, technical and administrative safety of workstations.
- Devices and Media Controls: the connectivity of devices and other media to the main PHI containing servers and the restricted accessibility of such servers to authorized individuals.
HIPAA Physical Security Compliance Procedure #
HIPAA physical security compliance is based on the above mentioned four basic parameters that are Facility Access Controls, Workstation Use, Workstation Security and Devices and Media Controls. The figure below represents the flow of the process to ensure the compliance of physical security of the highlighted four factors. Physical inspections from time to time with constant safeguarding, timely staff training and interviews, random technical checks of workstations, main server and networks inspection for any malware or loopholes. Also, documentation of the gathered information and auditing of the process from time to time is also essential to enhance the credibly of the system.
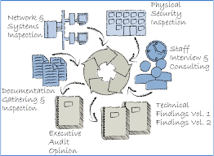
Who's and How's of HIPAA compliance #
The figure below sheds light on the importance of employees, company policy, firm processes and physical safeguarding of the systems for the purpose of HIPAA compliance. This video provides an understanding on how to improve privacy practices inside healthcare premises by ensuring HIPAA access control compliance. Also, HIPAA has provided a checklist on its website in an article named as HIPAA Compliance Checklist 2017. Lastly, Andrew Mitchell’s Better Access Control with Less Configuration: Ownership delivers some understanding of the who’s and how’s.

All healthcare premises, health insurers, and insuring clearance agents along with their business associates who might handle the PHI data typically have to be HIPAA compliant. This is possible by implementing secrecy of data, training employees, having HIPAA physical safeguards, and by following data privacy and authorization practices within their organization.
HIPAA Standard: Facility Access Control #
Here’s a typical scenario: Most companies usually get a key card (fob) system in place first. The downside? According to the requirements of the US HSS, most might not actually be complying with the standard.
Here is the original excerpt about the requirements in terms of access control by law:
Facility Access and Control. A covered entity must limit physical access to its facilities while ensuring that authorized access is allowed.
In brief, it mentions everything that is required from you to make your physical access and facility access HIPAA compliant. (If you're interested in the granular details of the standard, you can read the standards here). Most access control systems and offices might not be complying with the standards.
With keys, you obviously can’t limit authorized access once you gave out the key. People can easily pass the keys to unauthorized personnel. The switch from keys to key cards is also particularly motivated by such security fears and risks.
In a dissertation by Seymour E. Goodman and Herbert S. Lin of the Committee on Improving Cybersecurity Research in the United States, they wrote:
Because the intent of security is to make a system completely unusable to an unauthorized party but completely usable to an authorized one…
That’s why people traditionally used keycards to allow “authorized access”—keycard systems are meant to comply with the security measures and standards of the law. With smartphone access, you can use stronger, un-hackable credentials as an authorized way to access your facility.
Who says you have to use an access system, such as a key card system, that actually creates more trouble than usefulness? Other than the fact that it complies with the law.
Here are the 3 security measures a cloud-managed, modern access control system can add, in addition to HIPAA compliance. When deciding on a new access control system, compare this to key card systems, which lack these features and security measures.
- Managed access: You decide which access level an employee, freelancer, visitor or client has and which doors should be accessible for this access group.
- Real-time audit: At any time you can pull a report of real-time access events, including unsuccessful, unauthorized, or denied requests.
- Remotely disable physical access: Limit access to your facility remotely by disabling access from your smartphone instantly.
If you'd like to hear more about how your space can become HIPPA compliant, let us show you how easy it is and why many modern organizations use our cloud-based software to automate compliance. For more on visitor policies at work, you can read our article on managing workplace visitor policies or feel free to get in touch with one of our security consultants who can tell you more.
An additional note:
If you host a data center, you might also want to look at SSAE 16 SOC 2, Type 2 Certified Facilities-Controls-Process.
SSAE 16, also called Statement on Standards for Attestation Engagements 16, is a regulation created by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA) for defining how data centers report on compliance controls.
The SOC 2 framework is a comprehensive set of criteria, known as the Trust Services Principles.

