Allowing visitors into your workplace is an excellent way to build relationships with potential clients or partners, foster a positive impression of your organization, and demonstrate your professionalism. However, it can also make you vulnerable to certain security threats, such as theft and property damage.
A security-centered visitor management system enables you to create the welcoming experience your visitors deserve without putting your people or assets at risk. In this article, you’ll learn what a security visitor management system includes, why it’s integral to your physical security, and how you can successfully put one in place.

What is a security visitor management system? #
A security visitor management system is a technology solution designed to increase safety and minimize risks. It combines software and hardware to give you full control over visitor access to your building, automate entry processes, and close gaps in your security strategy.
Components of a visitor security system #
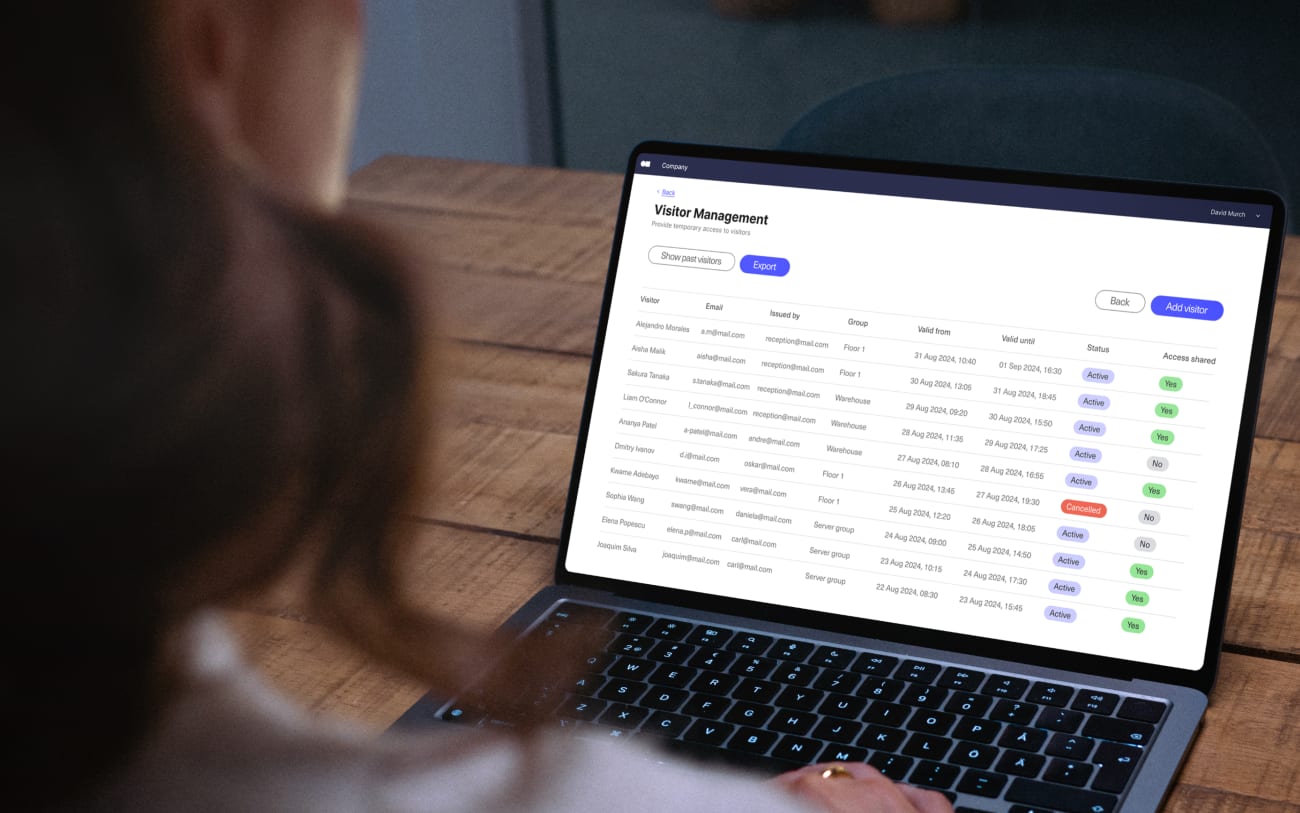
The purpose of a visitor management system is to allow you to screen, monitor, and track guests who enter your premises. Although some systems are more advanced than others, most have a few basic components:
- Software: Visitor management software allows you to access guest information and run reports using a mobile app or online dashboard. You can analyze traffic patterns and visitor habits to identify possible security vulnerabilities.
- Check-in kiosks: A visitor management and security kiosk enables guests to sign in when they arrive at your business. These kiosks automate the check-in process, so crowds don’t accumulate in your lobby or reception areas.
- Visitor logs: A security visitor management system also records information for every person who has visited the premises, including their name and contact information, in visitor logs. This data is vital when implementing emergency protocols or following up on security incidents.
- Badge printers: Many systems, including Kisi, are compatible with printers you can use to generate visitor badges. Displaying guest names is central to maintaining awareness and security on your property.
Along with these core functionalities, many visitor management systems also have advanced features. For example, some modern systems use artificial intelligence (AI) to analyze visitor activity and predict when security incidents might occur.
Security visitor management vs. basic sign-in tools #
If your organization relies on traditional sign-in sheets, you may be missing out on valuable security upgrades. A digital visitor management system has capabilities which simply aren’t possible with a paper log.
Automation is a large part of what sets apart modern visitor management tools. For example, when a visitor arrives on-site, the system can notify the host of their arrival, ensuring they are promptly greeted and don’t wander through the building unsupervised.
Digitization also allows for easier file storage and analytics. A visitor management system like Kisi can offer insights into patterns and trends in visitor behavior so you can adjust your staffing or security strategies. Basic sign-in tools make analytics difficult, time-consuming, and less detailed.

Why visitor management matters to physical security #
A visitor management system allows you to control, monitor, and log who enters your facility. By pre-screening visitors, verifying identities, and tracking guests, you can prevent unauthorized access and harmful criminal activity, including property damage, asset and data theft, and violence.
Visitor management devices, such as kiosks, are also a natural deterrent to security threats. If people with malicious intent know they can’t enter the premises without providing their personal information, they’re less likely to try to slip in undetected. In addition, displaying signs that your property is closely monitored suggests you have other security measures which make it easier to detect and react to on-site events.
This is especially important for hybrid, multi-tenant, or compliance-driven workplaces, where tracking visitor movements is more challenging and even minor security incidents can cause serious consequences. It’s equally vital in spaces that can be monetized, such as fitness, coworking, and flex spaces, because they are often open at late hours when no staff or security personnel are present.
Key features of a security-focused visitor management system #
An effective visitor management and security system does much more than capture guest names and save them for later reference. When you’re shopping for a solution for your organization, keep these features in mind.
Photo capture and badge printing #
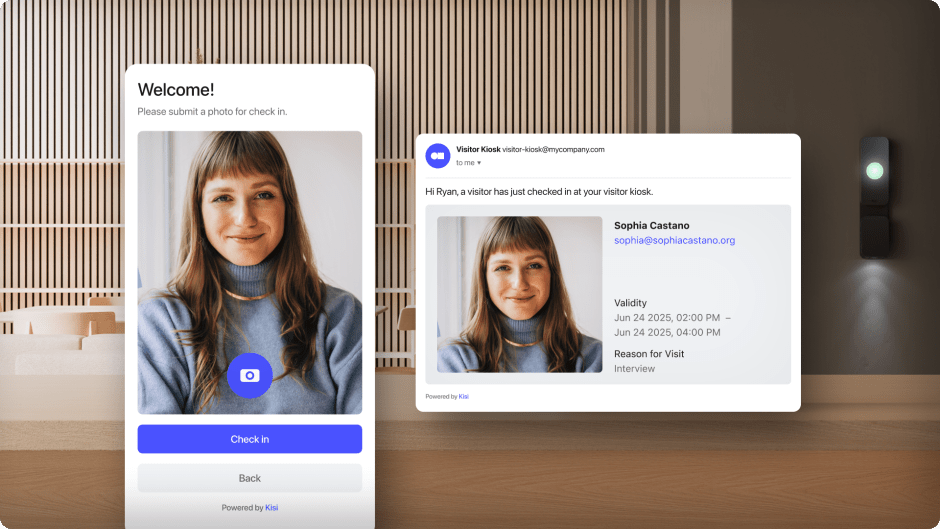
If you want your visitor management system to enhance your security, look for one that allows you to take photos of guests and print badges with their images. Capturing and displaying photos ensures visitors can’t use someone else’s badge to bypass your security protocols. It also allows for fast visual identification by security and other staff, which is especially important in high-security spaces.
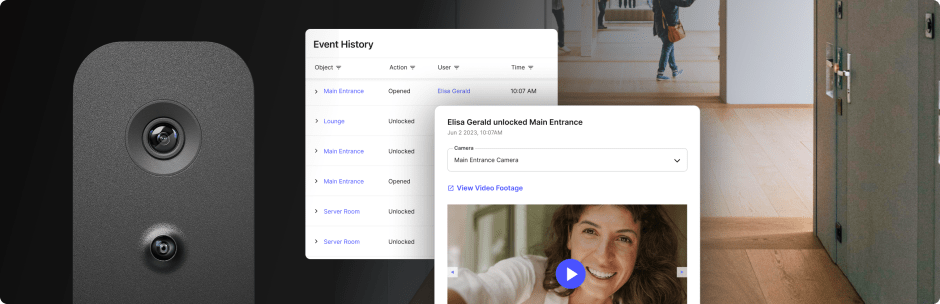
Real-time tracking #
Along with giving you a list of every person who has visited your site in the past, your visitor management system should also keep you up to date on who is on the premises at any given moment. A live dashboard that shows who is on the property and who they’re visiting is critical to safety and emergency response procedures. It allows security personnel, police, and other emergency responders to confirm the building has been cleared or quickly locate a criminal suspect.
ID verification #
A visitor management system also allows for instant ID verification. When a visitor signs in, the system can prompt them to scan their driver’s license or identification card. It then compares their name to the information entered and checks it against a list of flagged individuals, such as people who are banned from the site.
If the system can’t verify the guest’s identity or flags them as a security threat, it will reject their sign-in and can alert security personnel. This approach is faster than asking front-desk staff to run ID checks.
Integrations #
Connecting your visitor management system with other security devices and platforms, such as access control and video surveillance, further reduces your security risks. It gives you multiple forms of verification and follow-up, allowing you to thoroughly investigate security incidents and provide extensive evidence to law enforcement.
An effective system should allow you to integrate these systems and control them from a central dashboard, giving you a fuller picture of visitor activity. For example, if you use both video surveillance and visitor management, you can not only record the names of visitors but also get visual confirmation of their movements while on the property. Combining the elements of all these systems with an option like Kisi’s One Security Platform creates stronger protection for your business and streamlines your management processes.

Best practices for creating and implementing visitor security policies #
If your organization hasn’t used a visitor management system in the past or is upgrading from an outdated, inefficient solution like paper-based logs, adjusting your security approach can be intimidating. You have to research visitor management providers, find the best option for your organization, and train your employees in how to use it.
On top of those steps, you also need to ensure visitors understand your policies and know how to comply with them. To make sure employees and visitors alike embrace and use your visitor management system, you need to present it in a straightforward way that underscores its role in protecting your property.
Your specific visitor security policies and management solution will depend on your business location and security needs. To get started, follow these tips when developing your visitor security strategy:
- Establish a clear check-in process with steps guests must follow before, during, and after their arrival.
- Provide security instructions for visitors detailing what they need to bring with them, any items they can’t bring on the premises, and whether they need to check out when departing the building.
- Communicate expectations in advance by posting them on your website, including them in appointment confirmations, and adding them to your mobile app.
- Require identification to confirm visitor identities and check names against any security watchlists.
- Issue customized visitor badges with your organization’s name and logo so visitors can’t duplicate them.
- Pre-register visitors whenever possible so you can screen them prior to arrival and explain your security protocols upfront.
- Include legal documents — such as NDAs — during the check-in process so guests have to review and sign them before entering the building.
Putting together a comprehensive visitor security plan can be daunting. If you’re struggling, consider reaching out to a visitor management provider who has the expertise to address your concerns and help you make informed decisions.
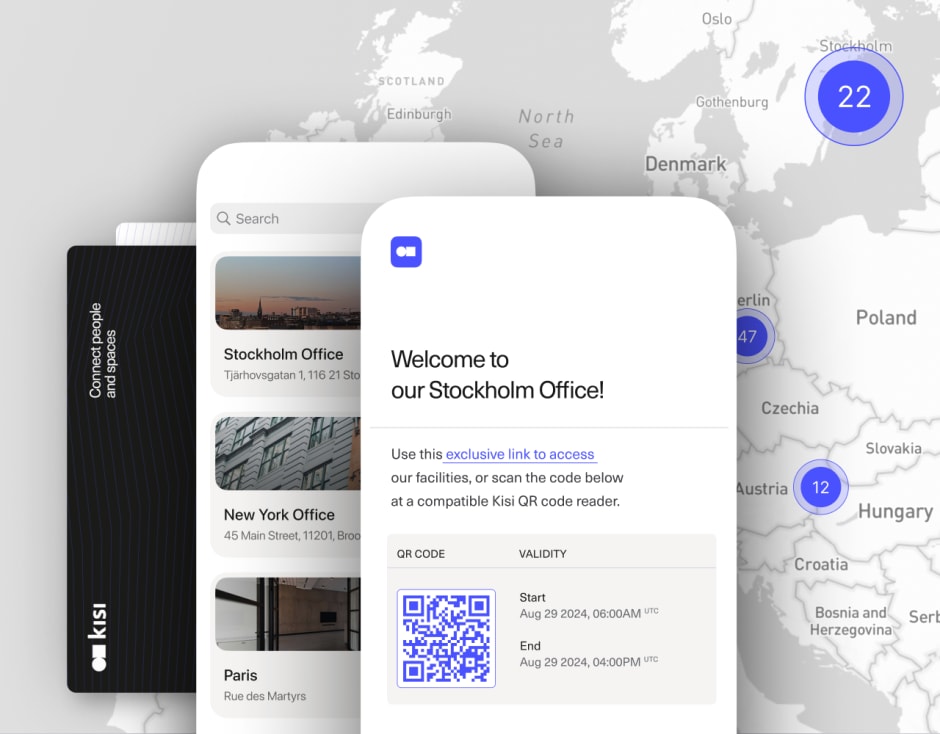
Explore visitor management and security solutions with Kisi #
When businesses think about physical security, they often focus exclusively on cameras, door locks, and intruder alerts. All those tools are vital, but don’t overlook the importance of visitor management. Monitoring and restricting the flow of visitors into your business helps eliminate unauthorized entries and promotes a feeling of safety among your staff.
Ready to see exactly what a security visitor management system can do for your organization? Kisi’s future-proof solution is ideal for a wide variety of organizations, from 24-hour gyms to hybrid offices to high-security manufacturing facilities. Get in touch with our team to try a demo, get a quote, or sign up for a free trial.

Vera Eftimovska
Marketing Campaign Manager at Kisi, blends her psychology background with hands-on experience in access control and workplace security. Passionate about how technology and human behavior intersect, she shares insights that help businesses build resilient, future-ready, and security-driven workplaces.