Guest management in a workplace environment refers to the processes used to register, identify, and control access for non-employees entering a facility. “Guests” is a general term, but one that includes anyone who requires temporary access to a physical space. They can be anything from partners, clients, contractors to interviewees, delivery personnel, etc.
Even though this term can be used interchangeably with visitor management, guest management focuses on the operational side of handling arrivals. A guest management system is the digital and physical infrastructure that makes a guest’s experience as seamless as an employee's. In this article, we’ll walk you through the components of a guest management system and how to implement it in your facility.

Guest check-in systems #
A guest check-in system is the operational core of guest management. A modern workplace doesn’t rely on paper sign-in sheets or manual reception logs anymore. They use structured digital workflows to manage guest arrivals from invitation to departure.
This process usually begins before the guest arrives. Hosts can pre-register expected visitors, collect required details (name, company, purpose of visit, etc.) and send confirmation instructions. Then, when the guest arrives on-site, check-in can take place through a self-service kiosk, tablet, or secure QR-based sign-in link. A guest sign-in app confirms the identity of the guests in question, allows them to review policies and, if needed, to complete any required acknowledgments.
Then, the system records the time of arrival and automatically notifies the host that their guest has arrived. Platforms that integrate guest check-in with access control, such as Kisi, extend this workflow further by linking registration directly to secure entry credentials.
Every check-in is logged centrally, so there is a guest record that can be reviewed later if needed. This digital record replaces fragmented manual logs so that guest activity is traceable, timestamped, and standardized across locations.
Guest badges and visual identification #
Guest badges are the visible layer of guest management. Digital systems are the ones that record visitor data behind the scenes, but badges make guest status immediately identifiable inside the building. A clearly marked guest badge helps employees recognize non-staff members, reinforces access boundaries, and reduces the likelihood of unauthorized movement.
After a successful check-in, a compatible badge printer can instantly produce a physical pass with the guest's name, photo, and the expiration date of their visit. Thus badges cannot be reused or mistaken for long-term credentials. Badge issuance can be automated as part of the check-in process. Integrated systems can also trigger badge printing immediately after a guest completes registration.
Guest access and entry controls #
It’s important to remember that guest registration alone does not control where a visitor can go. Once a guest has checked in, organizations must define what areas the individual is permitted to access and for how long. This authorization layer makes entry permissions align with the purpose and duration of the visit.
Temporary credentials can be configured with time-bound access windows that automatically expire after the visit ends. Access can also be restricted to specific doors or zones, preventing guests from moving freely throughout the facility. Integrated access control platforms, including Kisi, allow organizations to assign and revoke guest permissions dynamically, ensuring that registration and entry control function as connected but distinct processes.
For example, when a guest arrives at a secured door, they simply present their phone to a reader or tap a "one-click" link to unlock the door. These permissions are entirely customizable and thus an administrator can have full control over a guest’s access automatically so that it expires the moment their meeting ends.
For unannounced arrivals, intercom-based systems provide an additional control layer. Staff can verify the guest via video, approve entry remotely, so that access is logged in real time.

Guest policy in the workplace #
Guest management and compliance are detrimental to each other. Every company who has an influx of guests needs to have a visitor policy in place that can govern how these non-employees are registered, identified, and supervised within that facility.
A good policy clearly defines who is authorized to invite guests and what information must be collected prior to arrival. This can include everything from basic identification details, company affiliation to the purpose of visit, and acknowledgment of safety or confidentiality agreements.
Access rules should also be documented and any technical permissions should always be aligned with operational expectations. Organizations undergoing SOC2 or ISO audits must prove they have a consistent method for tracking non-employees. Guest logs should be retained for a defined period, accessible to authorized personnel, and reviewed when necessary. During emergencies, accurate guest records can support evacuation procedures.
The benefits of guest management software #
A structured guest management process provides plenty of benefits on the operational, security, compliance side in the workplace:
- Real-time visibility of on-site guests: centralized digital records make it easier to see who is currently in the building and when they arrived.
- Consistent policy enforcement: required information, acknowledgments, and approval workflows are standardized across locations and thus reducing reliance on manual oversight.
- Controlled and time-bound access: entry permissions can align with the purpose and duration of a visit and they minimize the risk of unauthorized access.
- Improved auditability and recordkeeping: timestamped logs create a clear historical record that can support any investigations, compliance checks, or internal reviews the company might have in the future.
- Reduced front-desk workload: self-service check-in workflows decrease manual data entry and administrative tasks.
- Scalability across multiple locations: digital systems allow organizations to apply the same guest management standards across offices, campuses, or facilities.
- Emergency preparedness: accurate guest logs improve accountability during evacuations.

How to implement a guest management system in the workplace #
If you want to implement a guest management software in your organization, there are some key requirements to look at:
Define your guest policy first #
As mentioned previously, any workplace needs to have a set of rules that will govern guest visits. You need to determine who is authorized to invite guests, what information must be collected before arrival, and whether approvals are required. Any escort expectations or access restrictions and data retention guidelines should also be clearly documented.
Map entry points #
Next, evaluate how guests move through the workplace. Identify primary and secondary entry doors, and determine where check-in stations or kiosks should be placed and also clarify which areas require restricted access. Digital workflows need to reflect real-world movement patterns and you need to have an admin view of the ecosystem.
Configure the workflow #
Configurization includes setting up pre-registration templates for hosts, customizing required sign-in fields or defining approval workflows when necessary, and standardizing badge issuance procedures. It’s important to create predictable, consistent processes across departments and locations.
Integrate with access control #
Guest registration should connect directly to entry authorization so that permissions align with the purpose and duration of each visit. Time-bound credentials, door-level restrictions, and automatic expiration rules help prevent lingering access once a visit concludes. Integrated access control platforms, such as Kisi, allow organizations to dynamically assign and revoke guest permissions, ensuring that registration and entry control function as connected but distinct processes.
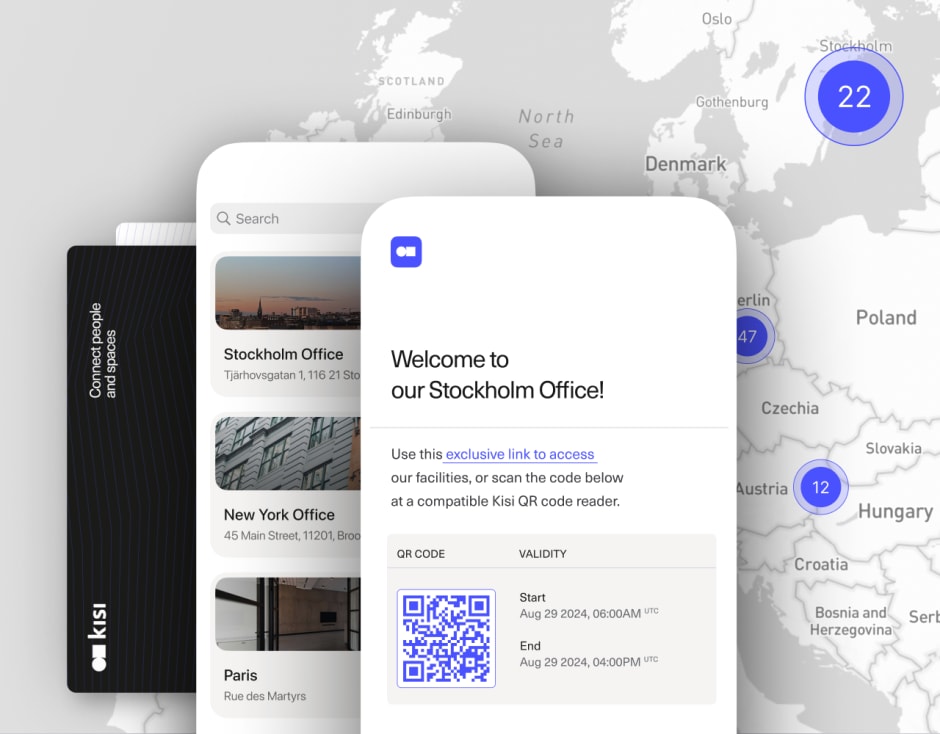
Turn guest management into a connected process with Kisi #
In the modern workplace, guest management has evolved beyond the generic logbook. It is no longer enough to simply know who is in your building. Now, you must have the operational tools to control where they go and how they experience your facility. If you integrate check-in workflows with physical access control, you eliminate security silos and create a "first impression" that doesn't compromise on safety.
Platforms like Kisi unify your sign-in flows, badge printing, and door hardware into a single ecosystem that makes every guest journey (from the initial invite to the final exit) secure and automated. If you have questions about how to unify your guest workflows and security into a single platform, contact our team to help you configure a setup.

Ana Coteneanu
Content writer @ Kisi | Ana focuses on long-form content that explores access control, space monetization, security, and modern workplace operations. With a background in technology-driven industries, she specializes in turning complex topics into practical insights for business audiences.