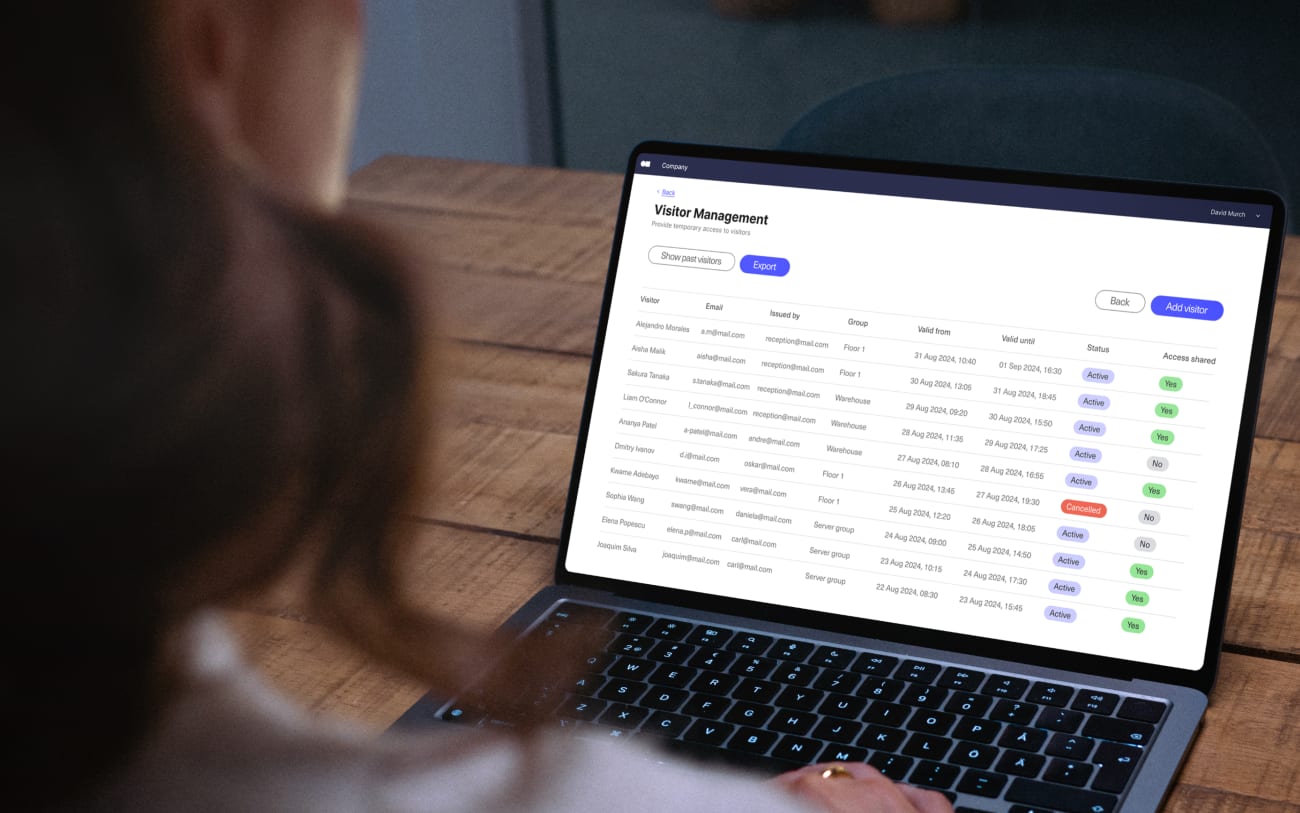
Managing visitors at your workplace involves more than just a sign-in sheet. With growing security concerns and increasing regulatory requirements, it's essential to have a system that not only tracks who’s entering your facility but also includes key features that improve security, streamline processes, and enhance the overall visitor experience. Choosing the right visitor management system (VMS) helps ensure your organization remains secure, compliant, and efficient.
This guide will walk you through the core and advanced features that should be part of every effective visitor management system, explain why each feature is important, and help you identify which ones are best suited to your organization’s specific needs. With many visitor management software options available, comparing their features can help you choose the best solution for your needs.
Why are visitor management features important? #
Visitor management systems do much more than just keep track of guests. They’re key to running smooth, secure, and compliant operations. Here’s why the features you choose can have a huge impact on both your business and visitors:
- Security: A VMS plays a crucial role in securing your workplace. By verifying identities and managing access with features like visitor access and sign-in, it ensures that only authorized visitors enter sensitive areas, minimizing risk and enhancing overall security.
- Compliance: Navigating compliance can be tricky, but the right tools make the process smoother. With automated visitor logs, digital document signing, and reporting, you’ll always be ready for audits and staying compliant with industry regulations like HIPAA or GDPR. Additionally, as outlined in the NIST Cybersecurity Framework 2.0, implementing a comprehensive visitor management system that integrates with access control is critical for meeting cybersecurity standards.
- Efficiency and visitor experience: No one likes to wait, especially vendors, delivery personnel, or potential clients. A VMS eliminates bottlenecks in the check-in process with features like automated badge printing and instant host notifications. With fewer manual tasks, your team can focus on more critical responsibilities, while visitors enjoy a smoother, quicker check-in experience, leaving with a positive first impression of your organization.
- Cost savings: While it might seem like an upfront investment, a VMS pays off by reducing manual tasks, cutting down on errors, and freeing up your team to focus on more important things. Plus, keeping security and compliance in check helps avoid costly mistakes and potential penalties.

Core features of visitor management systems #
A well-rounded visitor management system (VMS) provides several essential features that help keep your workplace secure and efficient. These features are the backbone of an effective system, ensuring smooth check-ins, better security, and a seamless experience for both visitors and staff.
Contactless self check-In #
Contactless self check-in has become an essential feature for modern visitor management systems. With QR code scanning or mobile apps, visitors can sign in quickly and without physical interaction, making it ideal for today’s health-conscious, fast-paced environment. This feature not only speeds up the check-in process but also enhances security by reducing the risk of human error.
The best part? It improves the overall visitor experience by eliminating long wait times at reception. Visitors also appreciate the convenience and peace of mind, knowing they can register for their visit safely without touching shared surfaces or handling physical materials. Plus, unlike paper check-in sheets, which can be easily accessed by other visitors, digital check-ins ensure that personal information remains secure and private.
Visitor registration #
The visitor registration process becomes faster and more efficient with digital systems. Rather than relying on paper logbooks, visitors can quickly input their details, such as name, company, and purpose of visit. This ensures an accurate and organized log of everyone entering your facility, which is key for both compliance and security.
With digital registration, your organization can maintain accurate, compliant records that are easily accessible for audits. Reduced wait times, along with enhanced security and professionalism, contribute to a smoother experience for both visitors and employees.
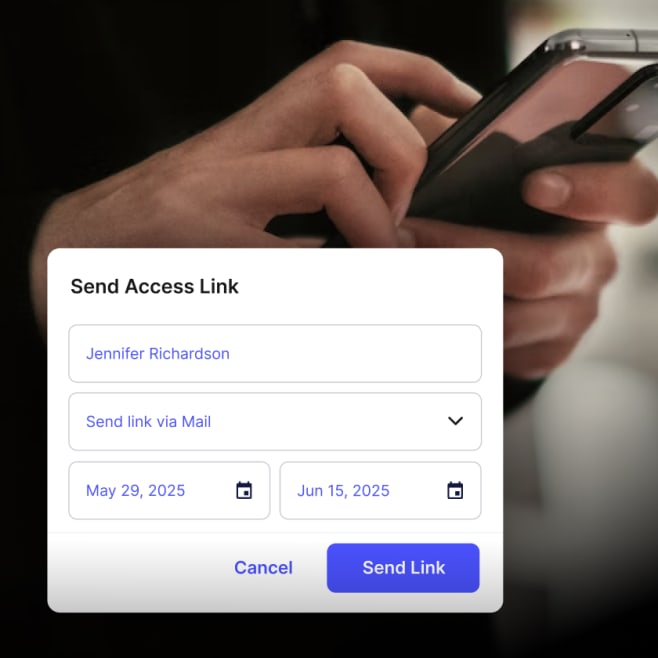
Basic visitor access #
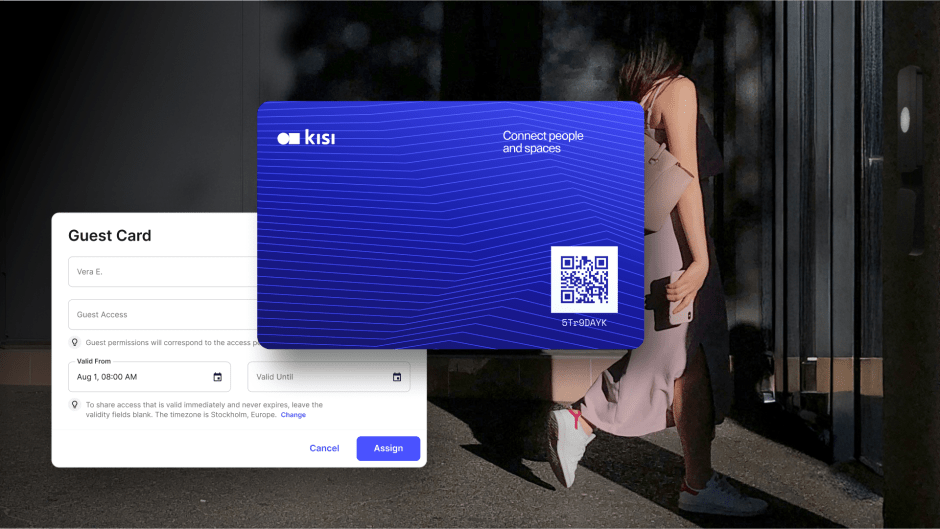
Visitor access allows guests to enter only the areas they are authorized to visit. A simple but effective method of granting access is by sending access links to visitors, which they can use to unlock doors connected to an access controller upon arrival.
These time-limited access links are sent via email or SMS, and visitors simply tap the link to gain entry. This process is quick, secure, and doesn’t require any app downloads, making it a user-friendly solution for managing guest access without the need for a physical key or manual check-in at the front desk. This method ensures that visitors are only able to enter designated areas, improving security without complicating the visitor experience.
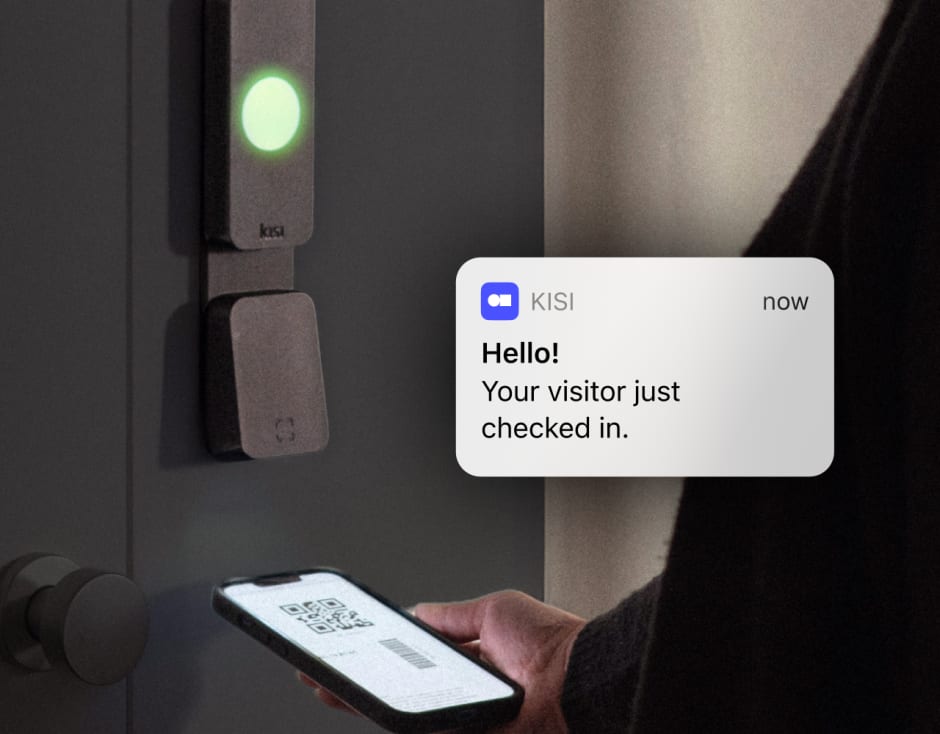
Host notifications #
When visitors arrive, it’s essential to alert the right person. Host notifications ensure that the relevant staff member is immediately informed of their visitor’s arrival, whether via email, SMS, or mobile app notification. This allows the host to be aware of their visitor and meet them promptly.
By eliminating the need for reception staff to manually notify hosts, this feature streamlines the check-in process and boosts efficiency. It also reduces visitor wait times, contributing to a smoother overall experience. Host notifications help keep everything coordinated, maintaining a professional, well-organized atmosphere and ensuring that visitors are greeted quickly and without unnecessary delays.
Automated badge printing #
Automated badge printing streamlines the visitor check-in process by instantly generating personalized visitor badges. These badges typically include essential information, such as the visitor’s name, photo, host details, access permissions, and time of visit. Visitors can quickly receive their badges as soon as they check in.
While automated badge printing is a core feature for larger offices or high-traffic environments, it may not be a necessity for smaller businesses with fewer visitors. However, for organizations looking to improve security and efficiency, this feature saves time at the front desk and reduces the risk of errors associated with manual badge creation. It also enhances security by ensuring badges are consistently formatted and easy to read, helping staff easily identify authorized visitors. Additionally, it improves the overall visitor experience by speeding up the check-in process and providing professional-looking badges upon arrival.
Advanced visitor management system features #
For organizations looking to enhance security, efficiency, and flexibility, advanced features can provide additional layers of customization and control. These features are particularly valuable for businesses with multiple locations, hybrid work practices, high-traffic areas, or specialized security needs. Advanced visitor management solutions offer more granular control and allow for a more seamless experience.
Visitor pre-registration and scheduling systems #
Visitor pre-registration and scheduling systems streamline the check-in process by allowing guests to register in advance. Visitors can input their details and select an appointment time through a web portal or email invitation, ensuring a more efficient arrival process.
Modern systems can automatically generate access credentials, send reminders, and coordinate with other facility resources like room bookings and parking spaces. By registering before arrival, visitors can bypass long check-in lines, allowing for a smoother and faster experience upon arrival.
This feature is especially beneficial for organizations hosting large numbers of visitors, such as corporate offices, event venues, or conference centers, helping manage visitor flow and ensure all necessary compliance documents (such as NDAs or safety waivers) are signed ahead of time.

Digital document signing #
Digital document signing allows visitors to electronically sign required documents, eliminating the need for paper-based forms and manual signatures. This feature is especially valuable for organizations that require visitors to acknowledge non-disclosure agreements (NDAs), waivers, safety protocols, or compliance documents before entering the facility.
Visitors can sign documents directly on their phones, tablets, or kiosks, and the signed copies are automatically stored in the system for future reference. This streamlines the check-in process, reduces paperwork, and ensures that all legal requirements are met with ease.
Digital document signing boosts efficiency by automating administrative tasks, reduces the risk of lost or incomplete forms, and ensures compliance with important industry regulations like HIPAA, GDPR, or OSHA. It also helps organizations avoid costly legal issues by ensuring that visitors acknowledge and sign the necessary documents in real time.
Mobile application management #
Mobile application management enables administrators to oversee visitor management operations from anywhere, providing full control on the go. With mobile apps designed for system monitoring, real-time notifications, and emergency management, administrators can respond to visitor activity without being tied to a desktop.
For administrators, the mobile app offers flexibility to track visitor arrivals, approve access, share QR codes and visitor links remotely, and manage emergency situations in real-time. Whether it's notifying hosts of visitor arrivals, managing multiple locations, or modifying visit details on the go, the mobile app ensures that administrators stay in control, no matter their location.
For visitors, the app enhances the check-in process by offering options for easy self-check-in and delivering digital access credentials directly to their inbox. This makes the experience quicker, safer, and more efficient.
This feature is particularly valuable for hybrid businesses, organizations with multiple locations, or companies with staff constantly on the move. Mobile application management enhances operational flexibility, improves response times, and ensures smooth visitor management, even during high-traffic periods or critical situations.
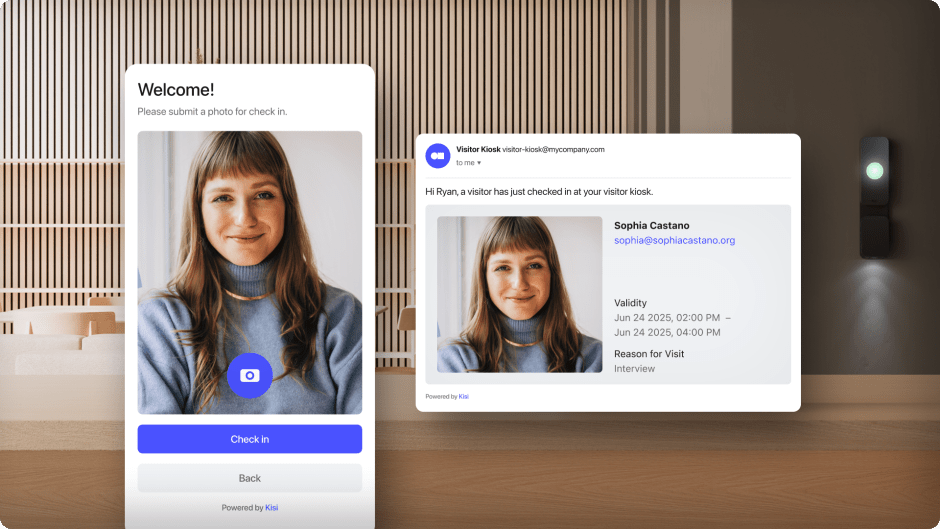
Visitor photo capture and identity verification #
During check-in, a visitor management system with photo capture takes a photo of the visitor, which is stored or printed alongside their registration details. This ensures that staff can verify the visitor’s identity against the stored photo, preventing unauthorized access by confirming that the person who checks in matches the photo on the badge.
For added security, the photo capture feature also makes it difficult for visitors to share their badges, as the photo can be referenced to ensure the right person is using the badge.
While basic photo capture is effective for many organizations, more advanced systems can enhance security by integrating biometric verification or comparing the photo to a government-issued ID for even higher levels of assurance.
In addition to photo capture, identity verification can involve cross-referencing the visitor’s details (such as name, date of birth, and government ID) with security databases or watchlists. This helps ensure that the visitor is not blacklisted or flagged for security concerns, offering a higher level of verification for environments that require additional security.

Centralized visitor access control #
Global access control provides a more advanced level of visitor management by allowing you to manage access across multiple locations remotely from a single, centralized dashboard. This ensures visitors are granted access based on their specific visit needs, no matter which facility they are visiting.
Modern systems enable administrators to provide QR codes or temporary access links, granting visitors entry to specific areas within a building or across multiple facilities. The central dashboard offers real-time control, enabling admins to manage visitor access, monitor activity, and make instant updates to access permissions across locations.
This feature is especially beneficial for organizations with multiple offices, campuses, or high-security areas. By managing visitor access from one centralized hub, businesses can enforce consistent security practices across all locations, simplifying the visitor management process for staff and guests.

Customizable reporting and analytics #
Customizable reporting and analytics give organizations the ability to extract valuable insights from their visitor data. With advanced visitor management systems, administrators can generate detailed reports that track visitor trends, security events, and operational efficiency.
Reports can be tailored to specific needs, such as visitor traffic patterns, peak visit times, security incidents, and compliance records. This helps organizations optimize resources, improve facility planning, and enhance security protocols. For example, tracking peak visitor times can help adjust staffing levels or optimize facility layouts to reduce congestion.
The integration of real-time analytics provides immediate visibility into visitor activity, enabling administrators to make informed decisions about security and operations.
Auditing and compliance tracking #
A strong auditing system is essential for ensuring compliance and maintaining security standards in visitor management. Advanced visitor management systems automatically generate detailed audit trails that record every interaction with the system, from check-in times and access points to document signings and visitor movements.
These audit trails are securely stored and can be accessed anytime for regulatory compliance or internal investigations. By maintaining comprehensive logs, businesses can provide transparent records for audits, ensuring they meet industry-specific standards.
The system’s ability to track and generate reports on visitor activity helps organizations manage risk and quickly identify any security breaches or compliance issues. Additionally, log retention policies allow businesses to store data for required timeframes, making it easier to respond to audits or legal inquiries.

Advanced integration capabilities and API access #
Advanced integration capabilities allow visitor management systems to seamlessly connect with other critical security and business systems, providing a unified solution for managing both visitors and overall operations. Using RESTful APIs, webhooks, and pre-built connectors, organizations can integrate their visitor management systems with platforms like human resources systems (HRIS), customer relationship management (CRM) tools, building management systems (BMS), and video surveillance networks.
These integrations help eliminate data silos and streamline workflows by automatically synchronizing visitor data with other business functions. For example, a law firm can link their visitor management system with case management software to automatically associate client visits with specific matters, or a healthcare facility can sync with patient management systems to enforce visiting hour policies.
Integrating visitor management with existing business systems improves data accuracy, reduces administrative overhead, and ensures a seamless experience for staff and visitors. It also strengthens security by enabling unified monitoring across various platforms, from visitor activity to building access, providing real-time insights into all aspects of operations. This level of integration is ideal for organizations that need to streamline processes, optimize resources, and enhance both security and visitor experience across their systems.
Emergency management and evacuation procedures #
Integrating visitor tracking with emergency procedures ensures organizations can respond efficiently during a crisis. In an emergency, the system can quickly provide a list of all visitors currently on-site, helping emergency responders identify who may need assistance.
Additionally, the system can integrate with building management systems to trigger automatic door unlocking, lockdowns, or mass notifications, improving coordination and response times during evacuations. This feature enhances safety by ensuring all visitors are accounted for and helps streamline evacuation procedures in critical situations.
How to Evaluate and Prioritize Features #
When evaluating a visitor management system, the key is to assess the unique needs of your organization. Features critical for one business may not be as essential for another. To make an informed decision, consider the following factors when evaluating and prioritizing features:
- Business type and industry requirements: Different industries have varying needs for security, compliance, and visitor tracking. For example, healthcare organizations may need advanced identity verification and compliance tracking to meet HIPAA regulations, while corporate offices may prioritize visitor pre-registration and real-time notifications. Consider your industry’s regulatory compliance and security standards when prioritizing features.
- Visitor volume: The number of visitors your facility sees can greatly influence the features you need. High-traffic facilities, such as conference centers, event venues, or multi-building campuses, may require visitor kiosks, pre-registration, and global access control. Smaller offices with fewer visitors may not need all of these features, and basic check-in and digital document signing may suffice.
- Security and access control setup: Consider your current security and access control infrastructure when evaluating a VMS. Does your organization already use electronic locks, video surveillance, or alarm systems? Ensure that the visitor management system integrates smoothly with these existing tools. Features like granular access control, centralized visitor access, and video surveillance integration can enhance security without replacing your current systems.
- Compliance and legal requirements: Organizations in industries with strict legal or compliance standards should prioritize features that help meet those requirements. Features like digital document signing, auditing and compliance tracking, and reporting and analytics are critical for staying compliant with regulations like GDPR, HIPAA, or PCI. Prioritize features that help automate and streamline your compliance processes.
- Operational efficiency and visitor experience: Consider how the system will impact your team’s daily workflow and the visitor experience. Features that automate tasks, such as visitor pre-registration, mobile app management, and digital document signing, can significantly improve efficiency and reduce administrative burden. On the visitor side, a system that offers contactless check-in and QR code entry will improve their experience and reduce wait times.
- Scalability and future growth: Think about your organization's future growth. Do you plan to expand to more locations or increase visitor volume? If so, features like centralized visitor access control, mobile management, and advanced integration capabilities are essential. Choose a system that can scale with your organization’s growth and evolving needs.
- Budget and cost considerations: While it's tempting to opt for every advanced feature, it’s important to balance functionality with your budget. Core features like visitor registration, badge printing, and host notifications may be sufficient for smaller businesses, while larger organizations may need more complex integrations and mobile app management. Prioritize based on what provides the most value for your specific requirements. Some systems, like Kisi, offer a free plan that provides basic visitor management functionalities, allowing you to evaluate features and add advanced ones as your business grows.
Ready to choose the right features for your business? #
Choosing the right visitor management system is a crucial decision that can significantly enhance your organization’s security, operational efficiency, and visitor experience. By carefully evaluating features that align with your needs, whether it’s contactless check-in, visitor access, compliance tracking, or mobile app management, you can select a system that meets your current needs and scales with your growth.
The ideal visitor management system should integrate smoothly with your existing infrastructure and offer an intuitive experience for both staff and visitors. With Kisi’s free plan, you can explore core features or start a free trial of the advanced plans to experience firsthand how a modern visitor management system can streamline operations and improve security with no upfront investment.
Still unsure which features are right for you? Get in touch with our security experts for a personalized demo and guidance on finding the perfect solution for your business.