Analyze Your Security Vulnerabilities and Needs #
Understanding security needs in order to keep your assets and facilities safe is of crucial importance. Think of all the access points that need to be secured (door entries, parking lot, gates, stockroom, server room, etc.). Do video surveillance and alarm monitoring need to be integrated in the system?
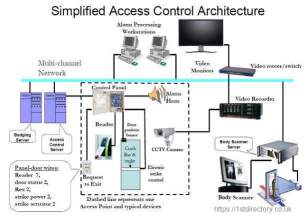
When designing access control, think about access criteria. Do visitors and contractors need to be identified? Will employees have different level of access depending on their role within the company? Is there any sensitive data that needs to be protected?
Define Budget #
Your access control design depends largely on the funds available. If your budget allocation for security is rather low, you might need to go for standalone access control. In case you have funds at your disposal or you are running a big organization with a lot of employees and access control points, then network access control with layered security is your best bet.
In case your access control design is based on networked solutions, think of type of access cards you would like to implement. You can choose among magnetic cards (cheaper option) or proximity cards (more long-lasting but also expensive compared to the magnetic cards), smart cards, tokens or go for biometic readers. The latter is the most expensive authentication tool.

Cooperate With Different Departments #
Planning access control should involve cooperation with various departments. No matter whether you go for a standalone or networked system, you will need assistance of IT personnel who will need to program the door units. Don’t forget about information security, where access control is needed as well.
Even the most sophisticated access control design won’t be effective enough if employees do not have policies and procedures to abide by. Planning access control presupposes having security policies implemented. That takes a joint effort of HR, legal and security departments.
Procure Smartly #
Create a comprehensive list of how you would like your access control system to look. Specify all the necessary details from applications you would like to integrate to access cards you are planning to use, and send the list to a few reliable vendors to benchmark the prices.
After you receive vendors’ replies with the price and confirmation that they can accomplish access control design that you’ve created, you need to make sure that you understood everything right.
It is advised that you double-check if the software vendors are offering is compatible with the hardware you have, and whether it is compatible with the cards you are planning to implement.
Proactivity is the best way to prevent some unexpected complications later on.
Once you make sure that access control design can be brought to realization and all the software and hardware is compatible, you can hire a vendor who will implement access control system.
Designing access control is not a simple thing to do. However, prior planning, careful analysis and joint effort of personnel from various departments will make it successful.

