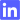At the annual security conference in Las Vegas, Defcon 2016, @jmaxxz, Anthony Rose and Ben Ramsey introduced different ways how bluetooth smart locks can be hacked [we were a little disappointed to not be included as we always like to be challenged on our security].
4 Devices to Get Hacking: #
- Passwords were transmitted in plain text, making it easy to extract passwords using a bluetooth sniffer like the Ubertooth One or Bleno.
- You’d need a Bluetooth Smart USB dongle to broadcast
- Raspberry Pi
- A high gain directional antenna

To make it easy for everyone we’ve summarized the main reasons why these locks were compromised:
- Replay attacks – simply recording and replaying the signal unlocks the lock.
- Vulnerable to fuzzing – meaning to change bytes of a valid command to get the lock into an error state that gets it to open. (Okidokey)
- Decompiling the APK used to unlock the smart lock by downloading the APK from the Android device, converting from dex to jar and then decompiling it. (Dana lock)
- Device spoofing (Bitlock Padlock)
- Adding a backdoor into the lock by a guest user allows to reset to factory settings and open lock. (August lock)
- Brute forcing because they only have 8 digit pins.
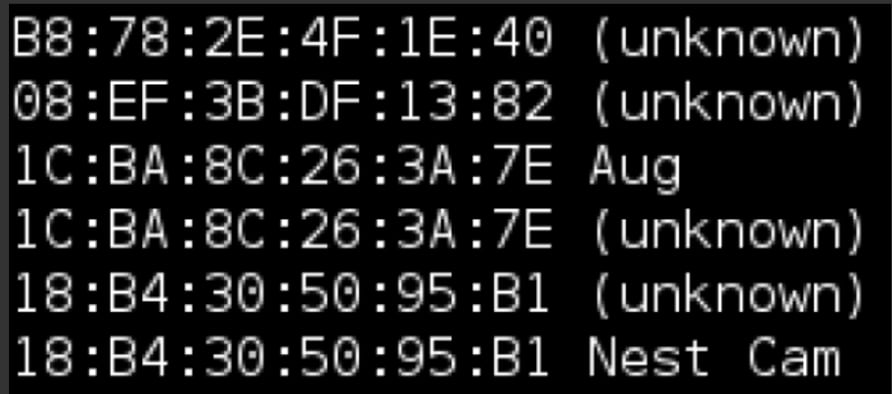
- Master API Admin code was hard coded in the hacked August Lock. Here are some of the original images:
Some features of the “uncrackable” smart locks:
- Proper AES encryption
- Truly random nonce (8 – 16 bytes)
- 2-factor authentication
- No hard coded passwords
- Long passwords allowed (16-20 characters)
Reading some of the comments in the Hackaday post suggests it will not take long till we see Bluetooth locks showing up in a CSI TV show. Let’s hope manufacturers will be more transparent with regards to their security standards and also communicate them to end users. In the end the strange thing about this whole discussion is that it’s not the lock that makes things secure, it’s the communication to and from the lock. Mechanics still work the same way they always did.