What are building entry systems? #
An entry system is the gatekeeper to your building and should regulate the security and flow of people with precision.
The main goal of entry systems is to grant access to authorized individuals and prevent unauthorized entry. This is achieved through an authentication process that requires access methods like key cards, smartphones, or advanced facial recognition systems.
Modern entry systems provide layered security, enabling precise control over access to specific areas at specific times. By effectively managing access, entry systems enhance overall security, protect valuable assets, safeguard sensitive information, and create a safer environment for people and spaces.
What are the different types of building entry systems? #
Building entry systems have evolved significantly over the years, providing improved security and convenience for various applications. Now there are numerous types of entry systems, including key-based and keyless entry systems: mobile, keypad, card access, and biometric systems.
Key-based systems: Key-based systems are the traditional method of access control and involve using physical keys to unlock doors or gates. While simple, they carry risks like duplication or loss. However, electronic locks and key tracking can bolster the security of these systems.
Keyless entry systems: These systems ditch traditional keys in favor of electronic devices like key fobs, cards, or smartphones. There are many types of keyless entry systems, which we cover in more detail below.
Mobile entry systems: These systems enable users to unlock doors with their smartphones. This technology is convenient and secure as people are likely to have their credentials close at hand at all times, and electronic passes can be easily revoked if the phone is lost. Kisi has 3 different unlock methods with mobile phones. This includes tap-in-app, tap-to-unlock, and MotionSense, where the door unlocks with a wave of the hand.
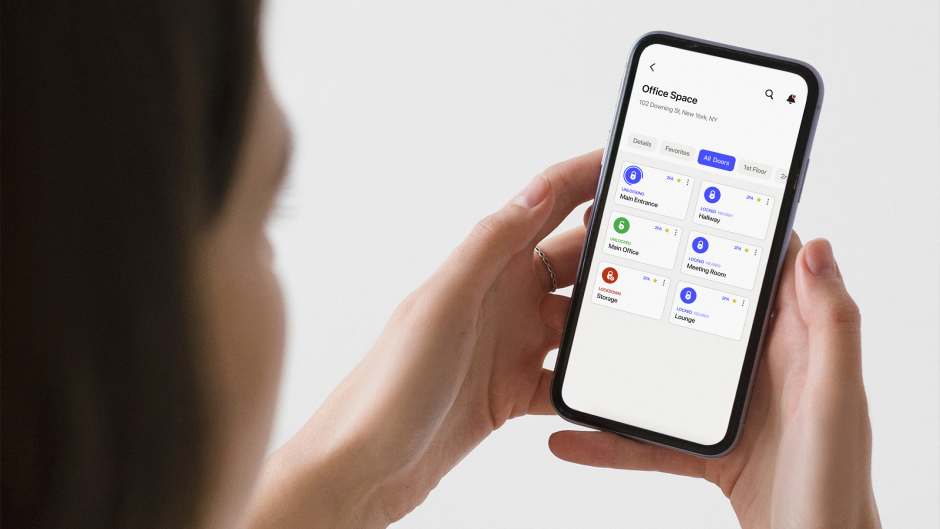
Keypad systems: In keypad systems, users enter a code on a numeric keypad for access. These systems are often used in commercial applications and can be standalone or part of a larger access control system. Regular code changes are vital to maintaining security.
Card access systems: Plastic cards or key fobs with electronic credentials are often used as access methods. Proximity or smart card readers validate the credentials, offering flexibility in issuance and deactivation. These are common in office buildings, hotels, and educational institutions.
Biometric access control systems: These rely on unique biological or behavioral traits for authentication, like fingerprints, iris patterns, facial features, or voice recognition. Biometrics offer robust security and are commonly found in high-security environments.
Seven things to consider when evaluating building entry systems #

When considering building entry systems, several factors need to be looked at to ensure their effectiveness and suitability for the specific application. Here is an outline of some key factors to consider:
- Security requirements: Determine the level of security required for the premises or facility. Consider the sensitivity of assets, potential risks, and the regulatory or compliance standards that must be met. You should choose an entry system with appropriate security features, such as strong encryption, multi-factor authentication, and intrusion detection.
- Budget: Set a realistic budget for upfront costs and ongoing expenses, including installation, maintenance, and licensing fees.
- Ease of setup: It’s important to secure your public entry spaces as early as possible. Consider the ease of setup and installation when looking at a new entry system. Kisi allows you to integrate with existing systems with zero downtime to quickly increase the security of your building.
- Scalability: Plan for future growth and ensure the system can accommodate increased users, entry points, multiple locations, and integration with other systems.
- User experience: Prioritize a system that is user-friendly, aligns with workflow requirements, and offers fast and easy access, including mobile compatibility.
- Integrations: Evaluate compatibility with current infrastructure, such as security and building management systems. Leverage existing investments where possible to minimize costs and streamline operations.
- Maintenance and support: Consider the level of technical expertise required for system maintenance, availability of vendor support, availability of training resources, and ease of troubleshooting.
Note: It is essential to consult with security professionals, system integrators, or access control experts to assess specific requirements and tailor the entry system accordingly.
Ready to speak to a security expert about door entry systems? Book in a free consultation with a Kisi security expert.
Placement of building entry systems #

Best practice design principles should guide the placement of access points, entry control protocols, and considerations for emergency situations.
When it comes to the placement of access points, analyzing the flow of people is crucial in determining the optimal locations based on traffic patterns, security needs, and convenience. Access points should be placed at primary entrances, high-traffic areas, and zones requiring restricted access, considering factors like natural surveillance, visibility, and environmental conditions.
In terms of entry control protocols, implementing appropriate measures helps regulate access. This may involve using different authentication factors such as mobile credentials, keycards, biometrics, or PIN codes. It's important to consider the required security level for different areas and tailor access control policies accordingly. For instance, you may want to implement two-factor authentication for high-security areas.
Entry systems should also be designed to handle emergencies effectively. Incorporating emergency override mechanisms allows quick and controlled access during fire alarms or power outages. Integrating emergency evacuation protocols with entry systems can facilitate swift and orderly evacuation. Features like remote lockdown can keep intruders in a secured space in case of an attack.
User-friendly design is paramount in entry systems to provide a smooth and efficient user experience. The system should provide clear instructions and feedback to guide users through the entry process. It's essential to consider the accessibility needs of all users, including individuals with disabilities, to ensure equal access and usability.
Integrating with other security components #

Integration of entry systems with security components such as surveillance systems, alarm systems, and building management systems enhances overall security, automation, and efficiency. Integrations are popular with employees too, as they help free up time and reduce mundane tasks. Property and facility managers have many repetitive administrative tasks that can be automated by connecting your systems and programming responses.
Here are some benefits of integrating building entry systems with these components.
Surveillance systems #
- Event-triggered recording: Access control events, like entry attempts, prompt the entry system to signal the surveillance system to start recording corresponding video footage. This synchronized recording streamlines post-event analysis and investigations.
- Live video monitoring: Security personnel can view live video feeds from surveillance cameras linked to specific access points, allowing for real-time identity verification, entry process monitoring, and swift response to security incidents.
- Video management and analytics: Add another layer of security with tailgating detection and operational insights with video management. Advanced video analytics integration enables intelligent features such as facial recognition, license plate recognition, and behavior analysis. Access control events can trigger these analytics, bolstering security measures and automating processes.
Alarm systems #
- Intrusion detection: Entry systems can be configured to trigger alarms when unauthorized access attempts occur, such as tampering with doors or forced entry. The entry system communicates with the alarm system to activate audible alarms, send alerts to security personnel, or initiate specific emergency protocols.
- Integration with access levels: By integrating access control with alarm systems, it is possible to create conditional rules. For example, if an individual with restricted access attempts to enter a secure area, the system can trigger an alarm, generating immediate attention or initiating a lockdown procedure.
Building Management Systems (BMS) #
- Energy efficiency: Integration allows the BMS to optimize energy consumption based on access control data. For example, the BMS can adjust lighting, heating, or cooling in specific areas based on occupancy information from the access control system, thereby reducing energy waste.
- Automation and occupancy management: Integration enables automated workflows, such as activating or deactivating access control systems based on building schedules or occupancy status. Access control events can trigger actions such as turning on/off lights, adjusting HVAC settings, or arming/disarming security systems.
- Centralized monitoring and reporting: Integration allows the BMS to receive access control data, providing a centralized dashboard for monitoring and generating reports. This consolidated view enhances situational awareness, simplifies administration, and enables data-driven decision-making.
Maintaining your building entry system #
Regular maintenance plays a critical role in achieving optimal performance. Routine maintenance tasks, such as system inspections and component checks, can identify and promptly address any potential issues or malfunctions.
Now, let's explore some helpful tips and best practices for troubleshooting common issues with entry systems.
For power-related problems, ensure that the entry system is connected to a reliable power source and has adequate backup options, such as battery backups or uninterruptible power supplies (UPS). Regularly test these backup systems to verify their functionality and runtime during power outages.
When users face access problems, verify that their credentials and access rights are correctly configured in the system's database. Testing the user's credentials on alternative access points or readers can also help identify whether the issue is isolated to a specific entry point.
Connectivity issues may arise if the entry system relies on network connectivity. Thoroughly inspect the network infrastructure, checking for any physical or configuration problems with network cables, switches, or routers. Ensure that the entry system's software and firmware are up to date to address any known connectivity issues or vulnerabilities. Kisi offers backup solutions in case you lose connectivity so you can have peace of mind knowing your building is secured and accessible regardless of your internet capabilities.
When troubleshooting complex issues, refer to the entry system's documentation, user manuals, and troubleshooting guides provided by the manufacturer. In cases where additional assistance is required, contacting the manufacturer's technical support or seeking guidance from qualified system integrators or service providers is advisable.
At Kisi, we provide thorough documentation and reliable support to make sure you always have the information you need.
Conclusion #
Building entry systems play a crucial role in regulating access, enhancing security, and improving people flow in a building. By understanding the different types of entry systems, their placement, integration options, and how to maintain your system, you can create a robust and reliable entry system for your building or space.
Looking to enhance your building access and security? Kisi’s industry-leading access control solution enables multiple unlock methods, including mobile devices, keycards, fobs, and third-party NFC and RFID credentials. Learn more about Kisi’s different access methods and the benefits of Kisi access control.

Rebekah May
Rebekah May is on a mission to increase awareness about the benefits of physical access control, and create safer spaces around the world.